As with information at rest, we should also map out the channels through which our information moves in order to identify ways to protect it.. Many of the information assets we have (especially in digital form) are frequently transported from one place to another: through text messages or messengers on our phones, emails, uploads or downloads to and from “cloud” services, phone calls, or even just browsing websites. However, many of the structures that we use for communicating important information in our human rights work are not designed to protect our information from surveillance. We may not be aware of this, nor do we often consider how our information may be intercepted by people opposed to our work.
Primarily our information is exposed in two broad instances:
Transfer: e.g. moving offices, sharing an attachment via email or backing-up sensitive files to another server.
Communications: e.g. when we speak on the phone, make video calls, hold meetings and events, and send email or text messages.
Therefore, we need to identify what information we share in these ways, in order to become aware of the threats to that information, and subsequently how we ought to protect it. To catalogue such information, in addition to the attributes mentioned for 'information at rest' [link], you can also think about how the information is transferred, its physical or virtual routes and who may be able to access it along the way.
Digital information
We should bear the following in mind when dealing with information in digital formats.
Replication: Digital information is constantly replicated. Every time a file is saved or altered or emailed, a copy is made. Bearing this in mind will improve our security strategy.
'Permanence' of information: As noted above, once a piece of information is uploaded to the internet, the process of upload, transfer and download entails multiple occasions where the information is copied. Our information can be retained in any of these locations and we are not in control of where, for how long, or by whom.
Metadata: Metadata is information created about and by the processes our computers and phones carry out. It can be very difficult to distort or hide metadata. Examples of metadata include:
-
Your IP address which locates where you are connecting to the internet, and the IP addresses of the websites you visit
-
the location data of your mobile phone as it moves from one point to another, and the unique identifying numbers of the SIM card and of the phone (known as the IMEI number). It is generally not possible to change your phone's IMEI.
-
the senders, recipients, time-stamps and subjects of emails, and whether they include attachments. This information cannot be erased, as servers need to know who to send the emails and its attachments. However, some of it can be changed or obscured.
-
information about the location in which a picture was taken, its size and the equipment used to produce the image (brand of camera and lens, software used to edit it) Some of this information can be erased using image processing software.
-
properties of a document, i.e. information about the author, the date in which a document was created or modified. Some of this information can be erased by changing the personal privacy settings of word or spreadsheets processors, or using a metadata stripping software such as the Metadata Anonymization Toolkit.
Because we don’t create it and may not even know it exists, metadata is often overlooked. However, we should keep it in mind and understand that although pieces of metadata may seem small or trivial, they can easily reveal many facts about us including locations we frequently visit and who belongs to our networks. Further, when taken on mass, metadata can also reveal our behaviour patterns and when we deviate from them.
Understanding information in motion through digital channels
Understanding now what examples of information in motion are, let’s look at the route of any piece of information as it 'travels' to the internet.
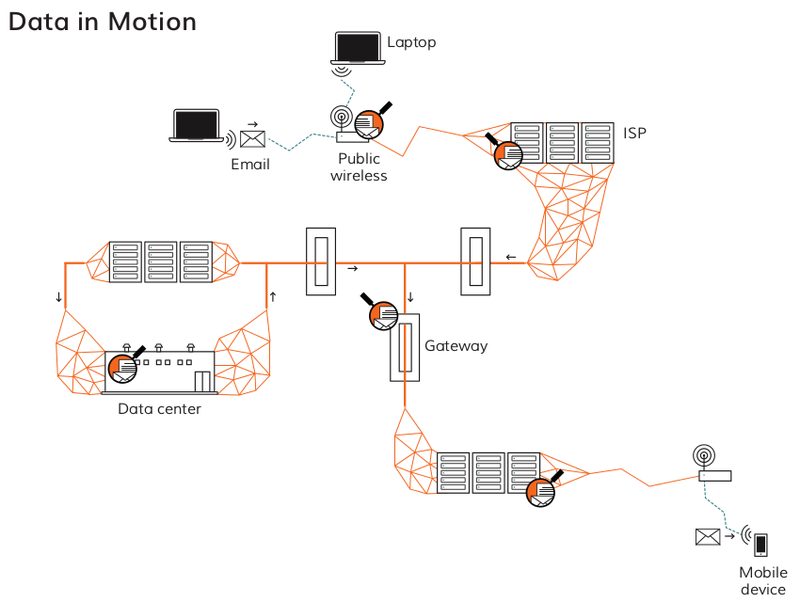
While we may know where our information originates (e.g. we type an email on our laptop), and where it will end up (e.g. our colleague's inbox via their mail provider), but we need also to pay attention to the stops along the way, including:
-
our router and local area network (LAN) at the office, at home or in the internet cafe: our activities online can be monitored or intercepted at this level
-
the internet service provider(s) and telecoms companies which operate the internet infrastructure and transfer our data
-
State entities who carry out active capturing and surveillance of data and metadata as it is transferred through the internet, such as at the country 'gateways'
-
other third parties like advertising companies who may gather data about our online activities
-
the providers of our online services such as email or social networking who may access, sell or hand over our data
The above information may mean you have to take out your actor map again and make some additions: who provides your internet access and online services such as email, social networking or “cloud storage”? Who controls the infrastructure? What is the relationship between these actors, and you, your allies and opponents?
The same questions should be posed regarding our use of mobile phones: who provides our services, including telephony and SMS, as well as the applications we use? What information can they access, and do we trust them with it?
Try using a table similar to the one below to map your information in motion.
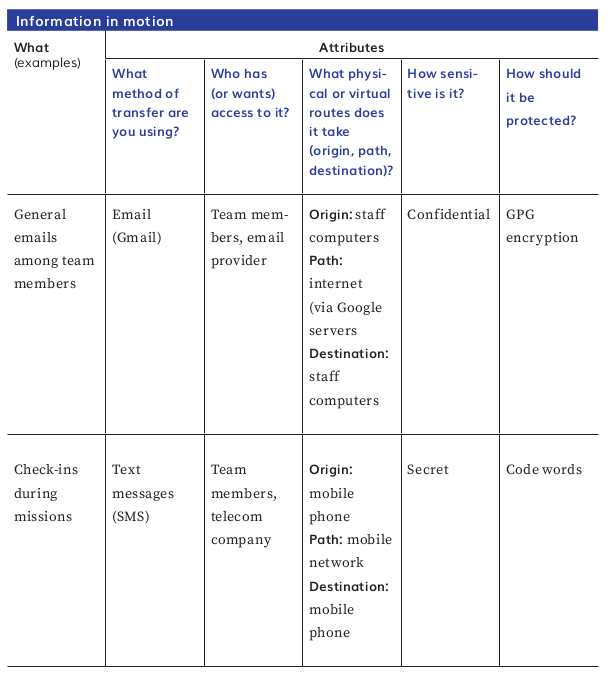
Having mapped out both your information in motion and your information at rest, consider what improvements you can make you your security strategy regarding your information. Consider implementing policies about who can access which information, or using software which protects your information, such as for securely deleting data from your devices or encrypting chats and emails.
For more information on how to secure your digital information, check out Security in-a-Box for practical strategies and hands on tips.
